tun2socks: Copy the whole doc.
This commit is contained in:
parent
d69b9dcb15
commit
48b324b9bf
217
linux/tun2socks/Benchmarks.md
Normal file
217
linux/tun2socks/Benchmarks.md
Normal file
|
|
@ -0,0 +1,217 @@
|
|||
# Introduce
|
||||
|
||||
Host connects to iPerf server with a 10G network card
|
||||
|
||||
### Platform A (Host)
|
||||
|
||||
Docker container
|
||||
|
||||
- **OS**: Arch Linux
|
||||
- **CPU**: Intel(R) Core(TM) i5-10500 CPU @ 3.10GHz
|
||||
- **Interfaces**:
|
||||
- eth0: 172.17.0.3
|
||||
|
||||
```
|
||||
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
|
||||
inet 172.17.0.3 netmask 255.255.0.0 broadcast 172.17.255.255
|
||||
ether 02:42:ac:11:00:03 txqueuelen 0 (Ethernet)
|
||||
RX packets 862435 bytes 112455267 (107.2 MiB)
|
||||
RX errors 0 dropped 0 overruns 0 frame 0
|
||||
TX packets 1215554 bytes 11083124435 (10.3 GiB)
|
||||
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
|
||||
```
|
||||
|
||||
### Platform B (iPerf3 Server)
|
||||
|
||||
Physical machine
|
||||
|
||||
- **OS**: Synology Linux
|
||||
- **CPU**: Intel(R) Atom(TM) CPU C3538 @ 2.10GHz
|
||||
- **Servers**:
|
||||
- Socks5 server listen on: `0.0.0.0:1080`
|
||||
- iPerf3 server listen on: `0.0.0.0:5201`
|
||||
- **Interfaces**:
|
||||
- ovs_eth4: 192.168.0.1
|
||||
- ovs_eth5: 192.168.1.1
|
||||
|
||||
```
|
||||
ovs_eth4 Link encap:Ethernet HWaddr 6C:92:BF:32:4C:2E
|
||||
inet addr:192.168.0.1 Bcast:192.168.0.7 Mask:255.255.255.248
|
||||
UP BROADCAST RUNNING MULTICAST MTU:9000 Metric:1
|
||||
RX packets:1549731 errors:0 dropped:0 overruns:0 frame:0
|
||||
TX packets:747607 errors:0 dropped:0 overruns:0 carrier:0
|
||||
collisions:0 txqueuelen:1
|
||||
RX bytes:56500520306 (52.6 GiB) TX bytes:274417116 (261.7 MiB)
|
||||
|
||||
ovs_eth5 Link encap:Ethernet HWaddr 6C:92:BF:32:4C:2F
|
||||
inet addr:192.168.1.1 Bcast:192.168.1.7 Mask:255.255.255.248
|
||||
UP BROADCAST RUNNING MULTICAST MTU:9000 Metric:1
|
||||
RX packets:21290414 errors:0 dropped:0 overruns:0 frame:0
|
||||
TX packets:12056862 errors:0 dropped:0 overruns:0 carrier:0
|
||||
collisions:0 txqueuelen:1
|
||||
RX bytes:240109208206 (223.6 GiB) TX bytes:8133459597 (7.5 GiB)
|
||||
```
|
||||
|
||||
# Pre-configuration
|
||||
|
||||
We create TUN interface on Host.
|
||||
|
||||
- Name: tun0
|
||||
- IP: 198.18.0.1
|
||||
- MTU: 9000
|
||||
|
||||
And then, `ip route add 192.168.1.1 dev tun0`
|
||||
|
||||
```
|
||||
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 9000
|
||||
inet 198.18.0.1 netmask 255.254.0.0 destination 198.18.0.1
|
||||
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
|
||||
RX packets 1290355 bytes 63071148 (60.1 MiB)
|
||||
RX errors 0 dropped 0 overruns 0 frame 0
|
||||
TX packets 2059447 bytes 11076291809 (10.3 GiB)
|
||||
TX errors 0 dropped 14 overruns 0 carrier 0 collisions 0
|
||||
```
|
||||
|
||||
# Benchmark
|
||||
|
||||
Note: we test upload/download speed with different number of connections, and we test multiple times to get an average result.
|
||||
|
||||
## Raw Speed
|
||||
|
||||
First, we test raw connection speed from Host to server using iperf3. And it reaches about >9 Gbits/sec (as expected).
|
||||
|
||||
Upload
|
||||
```
|
||||
$ iperf3 -c 192.168.0.1
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 7.30 GBytes 6.27 Gbits/sec 9 sender
|
||||
[ 5] 0.00-10.00 sec 7.29 GBytes 6.26 Gbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.0.1 -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 7.97 GBytes 6.84 Gbits/sec 6453 sender
|
||||
[SUM] 0.00-10.00 sec 7.91 GBytes 6.79 Gbits/sec receiver
|
||||
```
|
||||
|
||||
Download
|
||||
```
|
||||
$ iperf3 -c 192.168.0.1 -R
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 10.9 GBytes 9.41 Gbits/sec 11 sender
|
||||
[ 5] 0.00-10.00 sec 10.9 GBytes 9.40 Gbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.0.1 -R -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 11.0 GBytes 9.42 Gbits/sec 167 sender
|
||||
[SUM] 0.00-10.00 sec 11.0 GBytes 9.41 Gbits/sec receiver
|
||||
```
|
||||
|
||||
## badvpn-tun2socks
|
||||
|
||||
Second, we test the [badvpn-tun2socks](https://github.com/ambrop72/badvpn) project, which is directly installed using pacman on Arch Linux.
|
||||
|
||||
- Version: `BadVPN tun2socks 1.999.130`
|
||||
- Command Line: `badvpn-tun2socks --tundev tun0 --socks-server-addr 192.168.0.1:1080 --netif-ipaddr 198.18.0.1 --netif-netmask 255.255.254.0`
|
||||
|
||||
Upload
|
||||
```
|
||||
$ iperf3 -c 192.168.1.1
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ ID] Interval Transfer Bitrate Retr
|
||||
[ 5] 0.00-10.00 sec 803 MBytes 674 Mbits/sec 0 sender
|
||||
[ 5] 0.00-10.00 sec 802 MBytes 673 Mbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.1.1 -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 944 MBytes 792 Mbits/sec 10 sender
|
||||
[SUM] 0.00-10.00 sec 939 MBytes 788 Mbits/sec receiver
|
||||
```
|
||||
|
||||
Download
|
||||
```
|
||||
$ iperf3 -c 192.168.1.1 -R
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 3.35 GBytes 2.88 Gbits/sec 0 sender
|
||||
[ 5] 0.00-10.00 sec 3.34 GBytes 2.87 Gbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.1.1 -R -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 3.45 GBytes 2.96 Gbits/sec 1 sender
|
||||
[SUM] 0.00-10.00 sec 3.34 GBytes 2.87 Gbits/sec receiver
|
||||
```
|
||||
|
||||
## go-tun2socks
|
||||
|
||||
Then, we download the [go-tun2socks](https://github.com/eycorsican/go-tun2socks) binary from its original repo.
|
||||
|
||||
- Version: `v1.16.11`
|
||||
- Command Line: `tun2socks-linux-amd64 -proxyServer 192.168.0.1:1080 -tunName tun0 -tunPersist`
|
||||
|
||||
Upload
|
||||
```
|
||||
$ iperf3 -c 192.168.1.1
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 394 MBytes 331 Mbits/sec 0 sender
|
||||
[ 5] 0.00-10.00 sec 393 MBytes 329 Mbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.1.1 -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 399 MBytes 335 Mbits/sec 10 sender
|
||||
[SUM] 0.00-10.01 sec 392 MBytes 329 Mbits/sec receiver
|
||||
```
|
||||
|
||||
Download
|
||||
```
|
||||
$ iperf3 -c 192.168.1.1 -R
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 2.62 GBytes 2.25 Gbits/sec 0 sender
|
||||
[ 5] 0.00-10.00 sec 2.61 GBytes 2.24 Gbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.1.1 -R -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 3.00 GBytes 2.58 Gbits/sec 14 sender
|
||||
[SUM] 0.00-10.00 sec 2.91 GBytes 2.50 Gbits/sec receiver
|
||||
```
|
||||
|
||||
## tun2socks
|
||||
|
||||
Finally, let's test this project!
|
||||
|
||||
- Version: `v2.3.2`
|
||||
- Command Line: `tun2socks-linux-amd64 -device tun0 -proxy socks5://192.168.0.1:1080`
|
||||
|
||||
Upload
|
||||
```
|
||||
$ iperf3 -c 192.168.1.1
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 3.40 GBytes 2.92 Gbits/sec 951 sender
|
||||
[ 5] 0.00-10.00 sec 3.38 GBytes 2.91 Gbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.1.1 -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 5.55 GBytes 4.76 Gbits/sec 84 sender
|
||||
[SUM] 0.00-10.02 sec 5.53 GBytes 4.74 Gbits/sec receiver
|
||||
```
|
||||
|
||||
Download
|
||||
```
|
||||
$ iperf3 -c 192.168.1.1 -R
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[ 5] 0.00-10.00 sec 3.53 GBytes 3.03 Gbits/sec 0 sender
|
||||
[ 5] 0.00-10.00 sec 3.51 GBytes 3.02 Gbits/sec receiver
|
||||
|
||||
$ iperf3 -c 192.168.1.1 -R -P 10
|
||||
- - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
[SUM] 0.00-10.00 sec 8.60 GBytes 7.38 Gbits/sec 1 sender
|
||||
[SUM] 0.00-10.00 sec 8.51 GBytes 7.31 Gbits/sec receiver
|
||||
```
|
||||
|
||||
# Summary
|
||||
|
||||
For all scenarios of usage, tun2socks performs best.
|
||||
|
||||
It archives:
|
||||
- 70% raw speed upload
|
||||
- 78% raw speed download
|
||||
|
||||
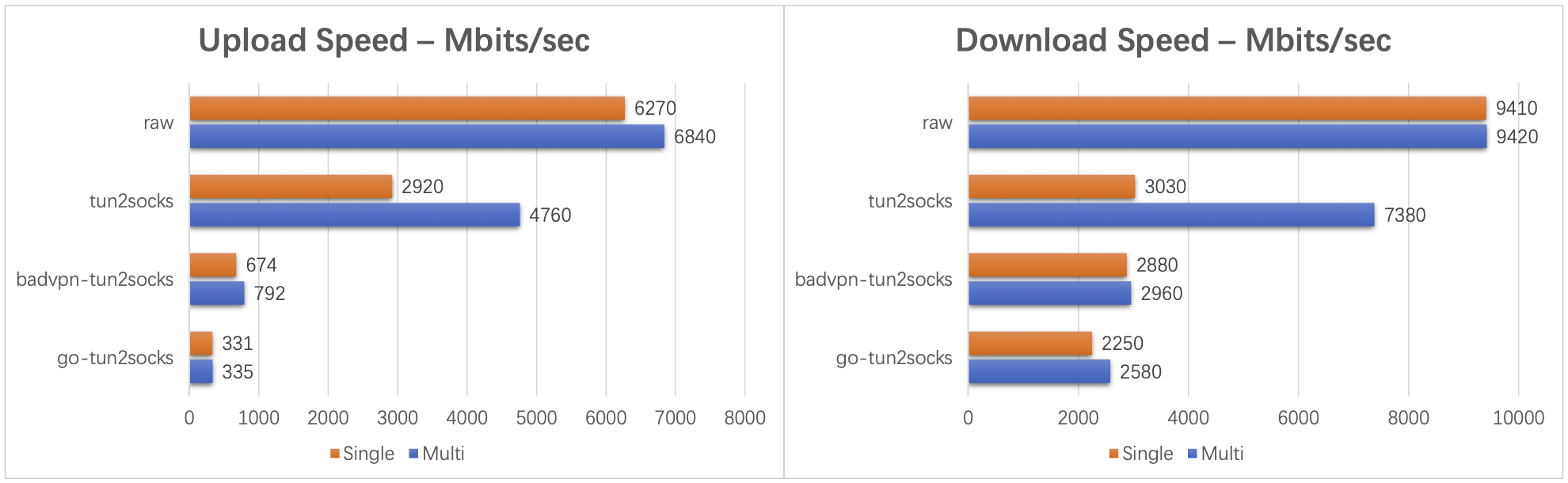
|
||||
68
linux/tun2socks/DNS-Configuration.md
Normal file
68
linux/tun2socks/DNS-Configuration.md
Normal file
|
|
@ -0,0 +1,68 @@
|
|||
## Set Up DNS
|
||||
|
||||
Currently, this tun2socks project is designed to perform a simply task:
|
||||
|
||||
```
|
||||
TCP/UDP packets <---(L3)---> [TUN Device <-> User-space TCP/IP stack] <---(L4)---> [Proxy Server]
|
||||
```
|
||||
|
||||
Which accepts incoming TCP/UDP packets through a TUN interface, and proxifies them through a proxy server.
|
||||
|
||||
The point is that tun2socks is not designed for DNS resolution, so users are responsible for setting up or configuring their own DNS servers.
|
||||
|
||||
To set up DNS in **Linux**, see:
|
||||
|
||||
- <https://www.cyberciti.biz/faq/howto-linux-bsd-unix-set-dns-nameserver/>
|
||||
|
||||
To set up DNS in **macOS**, see:
|
||||
|
||||
- <https://support.apple.com/en-ca/guide/mac-help/mh14127/mac>
|
||||
- <https://osxdaily.com/2015/06/02/change-dns-command-line-mac-os-x/>
|
||||
|
||||
To set up DNS in **Windows**, see:
|
||||
|
||||
- <https://tweaks.com/windows/40339/configure-ip-address-and-dns-from-command-line/>
|
||||
|
||||
For example, to set the DNS server address on a specified network interface to `8.8.8.8', do the following:
|
||||
|
||||
```sh
|
||||
netsh interface ipv4 set dns name="<Network Adapter>" static 8.8.8.8
|
||||
```
|
||||
|
||||
<!---
|
||||
## Remote DNS
|
||||
|
||||
Some proxy servers or protocols may not support UDP proxying, such as SSH tunnel, HTTP/SOCKS4 protocol; or you may want to have the proxy server resolve all DNS queries instead of resolving them locally, either to prevent DNS leaks or to circumvent local DNS censorship.
|
||||
|
||||
To achieve this goal, we can use...
|
||||
--->
|
||||
|
||||
## Hijack DNS
|
||||
|
||||
Sometimes some applications or programs may not follow the system's DNS settings, for example, they may have hardcoded their specified DNS server address into their program and bypass the system's name server resolution flow. In this case, DNS hijacking can be used to solve this kind of problem.
|
||||
|
||||
Please note that this method only applies to UDP-based DNS resolution, some TCP-based or DNS-over-HTTPS (DOH) resolutions can never be hijacked due to their security protections.
|
||||
|
||||
### Linux
|
||||
|
||||
Using `iptables` to redirect all DNS query to `8.8.8.8`
|
||||
|
||||
```sh
|
||||
iptables -t nat -A PREROUTING -p udp --dport 53 -j DNAT --to 8.8.8.8:53;
|
||||
iptables -t nat -A POSTROUTING -p udp -d 8.8.8.8 --dport 53 -o eth3 -j MASQUERADE;
|
||||
```
|
||||
|
||||
For example, we can redirect only cloudflare DNS query to `8.8.8.8`
|
||||
|
||||
```sh
|
||||
iptables -t nat -A PREROUTING -p udp -d 1.1.1.1,1.0.0.1 --dport 53 -j DNAT --to 8.8.8.8:53;
|
||||
iptables -t nat -A POSTROUTING -p udp -d 8.8.8.8 --dport 53 -o eth3 -j MASQUERADE;
|
||||
```
|
||||
|
||||
### Windows and macOS
|
||||
|
||||
Since the above two systems do not have `iproute2` support, DNS hijacking is relatively complicated on such systems. In macOS, Packet Filter (pf) could be used as an alternative, but I have not tested it yet.
|
||||
|
||||
Therefore, it is recommended to use mitm-based or customized proxy servers to implement proxy server-side DNS hijacking.
|
||||
|
||||
[V2ray](https://github.com/v2fly/v2ray-core) project can easily be adopted for this purpose, see this discussion: [v2fly/v2ray-core#2441](https://github.com/v2fly/v2ray-core/discussions/2441#discussioncomment-5457503)
|
||||
15
linux/tun2socks/Device-Models.md
Normal file
15
linux/tun2socks/Device-Models.md
Normal file
|
|
@ -0,0 +1,15 @@
|
|||
## Supported Device Models
|
||||
|
||||
### File Descriptor
|
||||
|
||||
`-device fd://<fd_int>`
|
||||
|
||||
### TUN Device
|
||||
|
||||
`-device tun://<tun_name>`
|
||||
|
||||
#### Options
|
||||
|
||||
- **GUID**
|
||||
- Persist GUID of network adapter (Windows Only) [#300](https://github.com/xjasonlyu/tun2socks/issues/300)
|
||||
- e.g. `tun://wintun?guid={7FE5A4A1-1326-40E2-974C-EF617156ACA8}`
|
||||
92
linux/tun2socks/Examples.md
Normal file
92
linux/tun2socks/Examples.md
Normal file
|
|
@ -0,0 +1,92 @@
|
|||
> Note: Please make sure that your proxy server is not running locally, e.g. `127.0.0.1:1080`, as this can cause an infinite route loopback problem. Some interface binding techniques can be used to solve this kind of problem, but users need to have enough network knowledge to solve it themselves.
|
||||
|
||||
## Linux
|
||||
|
||||
Create TUN interface `tun0` and assign an IP address for it.
|
||||
|
||||
```shell
|
||||
ip tuntap add mode tun dev tun0
|
||||
ip addr add 198.18.0.1/15 dev tun0
|
||||
ip link set dev tun0 up
|
||||
```
|
||||
|
||||
Configure the default route table with different metrics. Let's say the primary interface is `eth0` and gateway is `172.17.0.1`.
|
||||
|
||||
```shell
|
||||
ip route del default
|
||||
ip route add default via 198.18.0.1 dev tun0 metric 1
|
||||
ip route add default via 172.17.0.1 dev eth0 metric 10
|
||||
```
|
||||
|
||||
Start tun2socks and bind it to the primary interface.
|
||||
|
||||
```shell
|
||||
tun2socks -device tun0 -proxy socks5://host:port -interface eth0
|
||||
```
|
||||
|
||||
**Note**: sometimes we need to disable `rp_filter` for the corresponding interface so that it can receive packets from other interfaces.
|
||||
|
||||
```shell
|
||||
sysctl net.ipv4.conf.all.rp_filter=0
|
||||
sysctl net.ipv4.conf.eth0.rp_filter=0
|
||||
```
|
||||
|
||||
## macOS
|
||||
|
||||
In macOS, we need to start tun2socks first so that it will create TUN interface for us.
|
||||
|
||||
```shell
|
||||
tun2socks -device utun123 -proxy socks5://host:port -interface en0
|
||||
```
|
||||
|
||||
Use `ifconfig` to bring the TUN interface up and assign addresses for it.
|
||||
|
||||
```shell
|
||||
sudo ifconfig utun123 198.18.0.1 198.18.0.1 up
|
||||
```
|
||||
|
||||
Add these specific routes so that tun2socks can handle primary connections.
|
||||
|
||||
```shell
|
||||
sudo route add -net 1.0.0.0/8 198.18.0.1
|
||||
sudo route add -net 2.0.0.0/7 198.18.0.1
|
||||
sudo route add -net 4.0.0.0/6 198.18.0.1
|
||||
sudo route add -net 8.0.0.0/5 198.18.0.1
|
||||
sudo route add -net 16.0.0.0/4 198.18.0.1
|
||||
sudo route add -net 32.0.0.0/3 198.18.0.1
|
||||
sudo route add -net 64.0.0.0/2 198.18.0.1
|
||||
sudo route add -net 128.0.0.0/1 198.18.0.1
|
||||
sudo route add -net 198.18.0.0/15 198.18.0.1
|
||||
```
|
||||
|
||||
## Windows
|
||||
|
||||
To use it in windows, download [wintun](https://www.wintun.net/) to the tun2socks folder or the system PATH and start the program.
|
||||
|
||||
> In this example, "WIFI" is the default primary network interface.
|
||||
|
||||
```shell
|
||||
tun2socks -device wintun -proxy socks5://host:port -interface "WIFI"
|
||||
```
|
||||
|
||||
Same as macOS version, but we don't need to bring up the interface by hand, the only thing we need is to assign an IP address to it.
|
||||
|
||||
```shell
|
||||
netsh interface ipv4 set address name="wintun" source=static addr=192.168.123.1 mask=255.255.255.0
|
||||
```
|
||||
|
||||
In Windows, we usually need to manually set up the DNS address for our interface.
|
||||
|
||||
```shell
|
||||
netsh interface ipv4 set dnsservers name="wintun" static address=8.8.8.8 register=none validate=no
|
||||
```
|
||||
|
||||
Then route default traffic to TUN interface.
|
||||
|
||||
```shell
|
||||
netsh interface ipv4 add route 0.0.0.0/0 "wintun" 192.168.123.1 metric=1
|
||||
```
|
||||
|
||||
## Android
|
||||
|
||||
See this issue: [#123](https://github.com/xjasonlyu/tun2socks/issues/123)
|
||||
55
linux/tun2socks/Home.md
Normal file
55
linux/tun2socks/Home.md
Normal file
|
|
@ -0,0 +1,55 @@
|
|||

|
||||
|
||||
# Welcome
|
||||
|
||||
Welcome to the official Wiki page for [xjasonlyu/tun2socks](https://github.com/xjasonlyu/tun2socks).
|
||||
|
||||
# Quickstart
|
||||
|
||||
- Download precompiled binary from [Releases](https://github.com/xjasonlyu/tun2socks/releases)
|
||||
|
||||
```sh
|
||||
tun2socks --device tun://tun0 --proxy socks5://1.2.3.4:1080
|
||||
```
|
||||
|
||||
For detailed examples, see [this](https://github.com/xjasonlyu/tun2socks/wiki/Examples).
|
||||
|
||||
## Usage
|
||||
|
||||
```text
|
||||
Usage of tun2socks:
|
||||
-config string
|
||||
YAML format configuration file
|
||||
-device string
|
||||
Use this device [driver://]name
|
||||
-fwmark int
|
||||
Set firewall MARK (Linux only)
|
||||
-interface string
|
||||
Use network INTERFACE (Linux/MacOS only)
|
||||
-loglevel string
|
||||
Log level [debug|info|warning|error|silent] (default "info")
|
||||
-mtu int
|
||||
Set device maximum transmission unit (MTU)
|
||||
-proxy string
|
||||
Use this proxy [protocol://]host[:port]
|
||||
-restapi string
|
||||
HTTP statistic server listen address
|
||||
-tcp-auto-tuning
|
||||
Enable TCP receive buffer auto-tuning
|
||||
-tcp-rcvbuf string
|
||||
Set TCP receive buffer size for netstack
|
||||
-tcp-sndbuf string
|
||||
Set TCP send buffer size for netstack
|
||||
-tun-post-up string
|
||||
Execute a command after TUN device setup
|
||||
-tun-pre-up string
|
||||
Execute a command before TUN device setup
|
||||
-udp-timeout duration
|
||||
Set timeout for each UDP session
|
||||
-version
|
||||
Show version and then quit
|
||||
```
|
||||
|
||||
# License
|
||||
|
||||
This software is released under the [GPL-3.0](https://github.com/xjasonlyu/tun2socks/blob/main/LICENSE) open-source license.
|
||||
36
linux/tun2socks/Install-from-Source.md
Normal file
36
linux/tun2socks/Install-from-Source.md
Normal file
|
|
@ -0,0 +1,36 @@
|
|||
## Dependencies
|
||||
|
||||
Make sure the following dependencies are installed:
|
||||
|
||||
- Go >= 1.22
|
||||
- git
|
||||
- make
|
||||
|
||||
## Install
|
||||
|
||||
Simply use `go install`
|
||||
|
||||
```shell
|
||||
go install github.com/xjasonlyu/tun2socks/v2@latest
|
||||
```
|
||||
|
||||
## Build
|
||||
|
||||
Clone the project source code.
|
||||
|
||||
```shell
|
||||
git clone https://github.com/xjasonlyu/tun2socks.git
|
||||
```
|
||||
|
||||
Build and install the `tun2socks` binary.
|
||||
|
||||
```shell
|
||||
make tun2socks
|
||||
sudo cp ./build/tun2socks /usr/local/bin
|
||||
```
|
||||
|
||||
Or build for all architectures.
|
||||
|
||||
```shell
|
||||
make all-arch
|
||||
```
|
||||
76
linux/tun2socks/Interface-and-Routes.md
Normal file
76
linux/tun2socks/Interface-and-Routes.md
Normal file
|
|
@ -0,0 +1,76 @@
|
|||
## Linux
|
||||
|
||||
See also:
|
||||
|
||||
- <https://www.cyberciti.biz/faq/linux-ip-command-examples-usage-syntax/>
|
||||
- <https://www.linode.com/docs/guides/how-to-use-the-linux-ip-command/>
|
||||
|
||||
The syntax is as follows to add an IPv4/IPv6 address:
|
||||
|
||||
```sh
|
||||
ip addr add {ip_addr/mask} dev {interface}
|
||||
```
|
||||
|
||||
To add a new route, the syntax is:
|
||||
|
||||
```sh
|
||||
ip route add {NETWORK/MASK} via {GATEWAYIP}
|
||||
ip route add {NETWORK/MASK} dev {DEVICE}
|
||||
|
||||
## Add default route using ip ##
|
||||
ip route add default {NETWORK/MASK} dev {DEVICE}
|
||||
ip route add default {NETWORK/MASK} via {GATEWAYIP}
|
||||
```
|
||||
|
||||
For example, to add a plain route to network `192.168.1.0/24` via gateway `192.168.1.254`:
|
||||
|
||||
```sh
|
||||
ip route add 192.168.1.0/24 via 192.168.1.254
|
||||
```
|
||||
|
||||
## Darwin/BSD
|
||||
|
||||
See also:
|
||||
|
||||
- **macOS**:
|
||||
- <https://dev.to/dunithd/how-to-set-a-static-ip-address-in-macos-using-command-line-4j1b>
|
||||
- **BSD**:
|
||||
- <https://man.freebsd.org/cgi/man.cgi?route>
|
||||
- <https://man.freebsd.org/cgi/man.cgi?ifconfig>
|
||||
- <https://www.cyberciti.biz/faq/how-to-configure-static-ip-address-on-freebsd/>
|
||||
|
||||
To add an IPv4/IPv6 address in BSD family systems:
|
||||
|
||||
- **IPv4**: `ifconfig <interface> <address> netmask <netmask>`
|
||||
- **IPv6**: `ifconfig <interface> inet6 <address> prefixlen <prefixlength>`
|
||||
|
||||
To add routes in BSD family systems:
|
||||
|
||||
- **IPv4**: `route add -net <network_address/prefixlength> <local_address>`
|
||||
- **IPv6**: `route add -net -inet6 <network_address/prefixlength> <local_address>`
|
||||
|
||||
## Windows
|
||||
|
||||
See also:
|
||||
|
||||
- <https://techgenix.com/configurestaticipwiththenetshcommand-lineutility/>
|
||||
- Netsh Commands:
|
||||
- <https://learn.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts>
|
||||
- <https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc770948(v=ws.10)>
|
||||
- <https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc731521(v=ws.10)>
|
||||
|
||||
To add an IPv4/IPv6 address on Windows:
|
||||
|
||||
- **IPv4**: `netsh interface ipv4 set address <interface> static <address> <netmask>`
|
||||
- **IPv4**: `netsh interface ipv6 set address <interface> static <address/prefixlength>`
|
||||
|
||||
For example, to add a static IPv4 address for "NetLAN1" and specify both the subnet mask and gateway, type:
|
||||
|
||||
```sh
|
||||
netsh interface ipv4 set address "NetLAN1" static <ip_address> <subnet_mask> <gateway>
|
||||
```
|
||||
|
||||
To add routes on Windows:
|
||||
|
||||
- **IPv4**: `netsh interface ipv4 add route <network_address> <netmask> <interface> <nexthop>`
|
||||
- **IPv4**: `netsh interface ipv6 add route <network_address/prefixlength> <interface> <nexthop>`
|
||||
19
linux/tun2socks/Load-TUN-Module.md
Normal file
19
linux/tun2socks/Load-TUN-Module.md
Normal file
|
|
@ -0,0 +1,19 @@
|
|||
If some Linux releases need to load the TUN device (`dev/net/tun`) manually, please use the following script:
|
||||
|
||||
```sh
|
||||
#!/bin/sh
|
||||
|
||||
# Create the necessary file structure for /dev/net/tun
|
||||
if [ ! -c /dev/net/tun ]; then
|
||||
if [ ! -d /dev/net ]; then
|
||||
mkdir -m 755 /dev/net
|
||||
fi
|
||||
mknod /dev/net/tun c 10 200
|
||||
chmod 0755 /dev/net/tun
|
||||
fi
|
||||
|
||||
# Load the tun module if not already loaded
|
||||
if ( ! (lsmod | grep -q "^tun\s")); then
|
||||
insmod /lib/modules/tun.ko
|
||||
fi
|
||||
```
|
||||
15
linux/tun2socks/Memory-Optimization.md
Normal file
15
linux/tun2socks/Memory-Optimization.md
Normal file
|
|
@ -0,0 +1,15 @@
|
|||
This tun2socks project is designed for best performance, so the memory consumption might be relatively high sometimes.
|
||||
|
||||
However, starts with `v2.4.0`, there are three tcp options added for tun2socks: `tcp-sndbuf`, `tcp-rcvbuf`, `tcp-auto-tuning`.
|
||||
|
||||
- `tcp-sndbuf`: TCP send buffer size
|
||||
- `tcp-rcvbuf`: TCP receive buffer size
|
||||
- `tcp-auto-tuning`: TCP moderate receive buffer auto-tuning
|
||||
|
||||
The default value for send/receive buffer size is ~~212 KiB~~1MiB, and the receive buffer auto-tuning is disabled by default now (note that this option is enabled by default before `v2.4.0`).
|
||||
|
||||
To optimize the memory usage in different systems, we can properly adjust the buffer size.
|
||||
|
||||
If you have enough memory resource available, you can set large buffer size, e.g., `2-4m`, and even turn on the `tcp-auto-tuning` option. This operation will consume a lot RAM, but throughput would be increased.
|
||||
|
||||
In memory insufficient/sensitive system, it's recommended to set small buffer size, e.g., `16-64k`. Small buffer size can reduce memory usage and sometimes it can even less 80% RAM compared to large buffer size.
|
||||
63
linux/tun2socks/Proxy-Models.md
Normal file
63
linux/tun2socks/Proxy-Models.md
Normal file
|
|
@ -0,0 +1,63 @@
|
|||
## Syntax of Supported Proxy Models
|
||||
|
||||
### HTTP
|
||||
|
||||
> HTTP proxy server must support **CONNECT** method!
|
||||
|
||||
`-proxy http://server_host:port`
|
||||
|
||||
### Socks4
|
||||
|
||||
> Socks4 only support **USERID** auth.
|
||||
|
||||
`-proxy socks4://<userid>@server_host:port`
|
||||
|
||||
### Socks5
|
||||
|
||||
`-proxy socks5://<username>:<password>@server_host:port`
|
||||
|
||||
Or for Unix Domain Socket (UDS)
|
||||
|
||||
`-proxy socks5:///path/to/file`
|
||||
|
||||
> Please note that connecting with UDS is not a standard Socks5 protocol and requires server-side support.
|
||||
|
||||
### Shadowsocks
|
||||
|
||||
`-proxy ss://method:password@server_host:port/<?obfs=http;obfs-host=xxx>`
|
||||
|
||||
or in [SIP002](http://shadowsocks.org/en/wiki/SIP002-URI-Scheme.html) URI scheme:
|
||||
|
||||
`-proxy ss://base64_encode(method:password)@server_host:port/<?obfs=http;obfs-host=xxx>`
|
||||
|
||||
P.S. Leave method and password empty to use none cipher mode.
|
||||
|
||||
### Relay
|
||||
|
||||
> Latest [GOST](https://github.com/go-gost/gost) version is required for better compatibility.
|
||||
|
||||
`-proxy relay://<username>:<password>@server_host:port?<nodelay=false>`
|
||||
|
||||
### Direct
|
||||
|
||||
> Note that `Direct` is usually used for testing purposes.
|
||||
|
||||
`-proxy direct://`
|
||||
|
||||
### Reject
|
||||
|
||||
> `Reject` simply blocks all outgoing connections.
|
||||
|
||||
`-proxy reject://`
|
||||
|
||||
## UDP Support Table
|
||||
|
||||
| Proxy | UDP Support | UDP Type |
|
||||
| ----- | :---: | :---: |
|
||||
| HTTP | ❌ | N/A |
|
||||
| Socks4 | ❌ | N/A |
|
||||
| Socks5 | ✅ | UDP |
|
||||
| Shadowsocks | ✅ | UDP |
|
||||
| Relay | ✅ | UDP over TCP |
|
||||
| Direct | ✅ | UDP |
|
||||
| Reject | N/A | N/A |
|
||||
5
linux/tun2socks/Source.md
Normal file
5
linux/tun2socks/Source.md
Normal file
|
|
@ -0,0 +1,5 @@
|
|||
# tun2socks sources.
|
||||
|
||||
[Repo](https://github.com/xjasonlyu/tun2socks)
|
||||
|
||||
[Wiki](https://github.com/xjasonlyu/tun2socks/wiki)
|
||||
26
linux/tun2socks/TUN-Pre-and-Post-UP.md
Normal file
26
linux/tun2socks/TUN-Pre-and-Post-UP.md
Normal file
|
|
@ -0,0 +1,26 @@
|
|||
Sometimes we want to run some commands before or after the TUN device is started, so there are two `tun-pre-up` and `tun-post-up` args that can be used in such scenarios.
|
||||
|
||||
- **TUN-Pre-UP**: The commands specified in the `tun-pre-up` option are executed before the TUN device is created.
|
||||
- **TUN-Post-UP**: The commands specified in the `tun-post-up` option are executed after the TUN device has been created.
|
||||
|
||||
For example, if we want to run a script to automatically configure the ip address for our interface addresses and routes, we can use `tun-post-up` arg like this:
|
||||
|
||||
```sh
|
||||
--tun-post-up "./your_script.sh"
|
||||
```
|
||||
|
||||
> Please note that the script you provided must have the execution permission.
|
||||
|
||||
### Multiple Commands
|
||||
|
||||
If we want to run multiple commands with `tun-pre-up` or `tun-post-up` args, we can call a shell to do the trick, e.g.:
|
||||
|
||||
```sh
|
||||
--tun-post-up "sh -c 'echo 1234567890 > a.txt && ./run_some_scripts.sh && rm -rf a.txt'"
|
||||
```
|
||||
|
||||
OR in Windows:
|
||||
|
||||
```sh
|
||||
--tun-post-up "powershell -Command 'command1 ; command2 ; command3'"
|
||||
```
|
||||
64
linux/tun2socks/Use-docker-compose.md
Normal file
64
linux/tun2socks/Use-docker-compose.md
Normal file
|
|
@ -0,0 +1,64 @@
|
|||
## Notes
|
||||
|
||||
We must use docker-compose version 2, since version 3 doesn't support user to specify network gateways.
|
||||
|
||||
## Example
|
||||
|
||||
docker-compose.yml
|
||||
|
||||
```yaml
|
||||
version: '2.4'
|
||||
|
||||
services:
|
||||
tun2socks:
|
||||
image: ghcr.io/xjasonlyu/tun2socks:latest
|
||||
mem_limit: 1000000000
|
||||
memswap_limit: 2000000000
|
||||
mem_reservation: 512m
|
||||
cap_add:
|
||||
- NET_ADMIN
|
||||
devices:
|
||||
- '/dev/net/tun:/dev/net/tun'
|
||||
environment:
|
||||
- LOGLEVEL=info # default
|
||||
- TUN=tun0 # default
|
||||
- ADDR=198.18.0.1/15 # default
|
||||
- MTU=9000 # default
|
||||
- PROXY= # *required
|
||||
- STATS=:8080 # optional
|
||||
- RESTAPI= # optional
|
||||
- TCP_SNDBUF=. # optional
|
||||
- TCP_RCVBUF=. # optional
|
||||
- TCP_AUTO_TUNING=. # optional
|
||||
- UDP_TIMEOUT= # optional
|
||||
- EXTRA_COMMANDS= # optional
|
||||
- TUN_INCLUDED_ROUTES= # optional
|
||||
- TUN_EXCLUDED_ROUTES= # optional
|
||||
# - GODEBUG=madvdontneed=1 # optional
|
||||
networks:
|
||||
switch:
|
||||
ipv4_address: 172.20.1.2
|
||||
sysctls:
|
||||
- net.ipv4.ip_forward=1
|
||||
# - net.ipv4.conf.all.rp_filter=0
|
||||
restart: unless-stopped
|
||||
container_name: tun2socks
|
||||
|
||||
networks:
|
||||
switch:
|
||||
name: switch
|
||||
ipam:
|
||||
driver: default
|
||||
config:
|
||||
- subnet: '172.20.1.0/25'
|
||||
gateway: 172.20.1.1
|
||||
driver: macvlan
|
||||
driver_opts:
|
||||
parent: eth0
|
||||
```
|
||||
|
||||
## Start
|
||||
|
||||
```sh
|
||||
docker-compose up -d
|
||||
```
|
||||
Loading…
Reference in a new issue